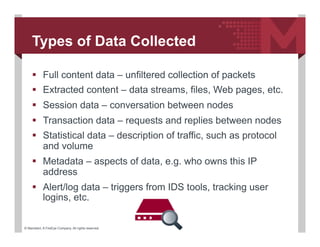
Anomaly Detection Mechanism based on Common NSM Data Objects for Advanced Metering Infrastructure | Semantic Scholar

LFN Webinar: Building CNFs with FD.io VPP and NSM + VPP traceability in cloud-native deployments - YouTube

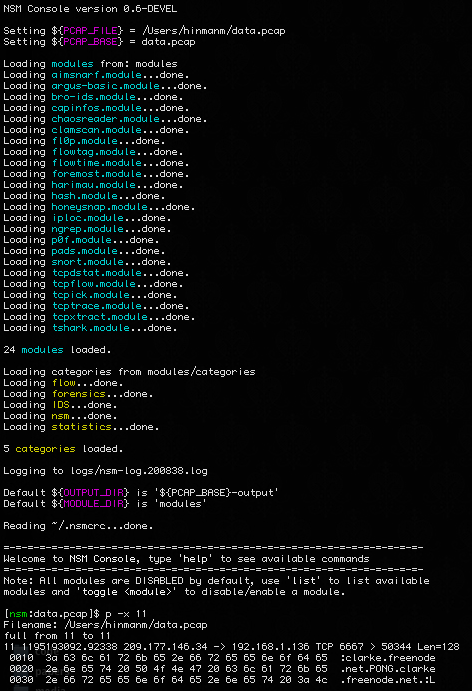
Intrusion Detection of NSM Based DoS Attacks Using Data Mining in Smart Grid – topic of research paper in Electrical engineering, electronic engineering, information engineering. Download scholarly article PDF and read for

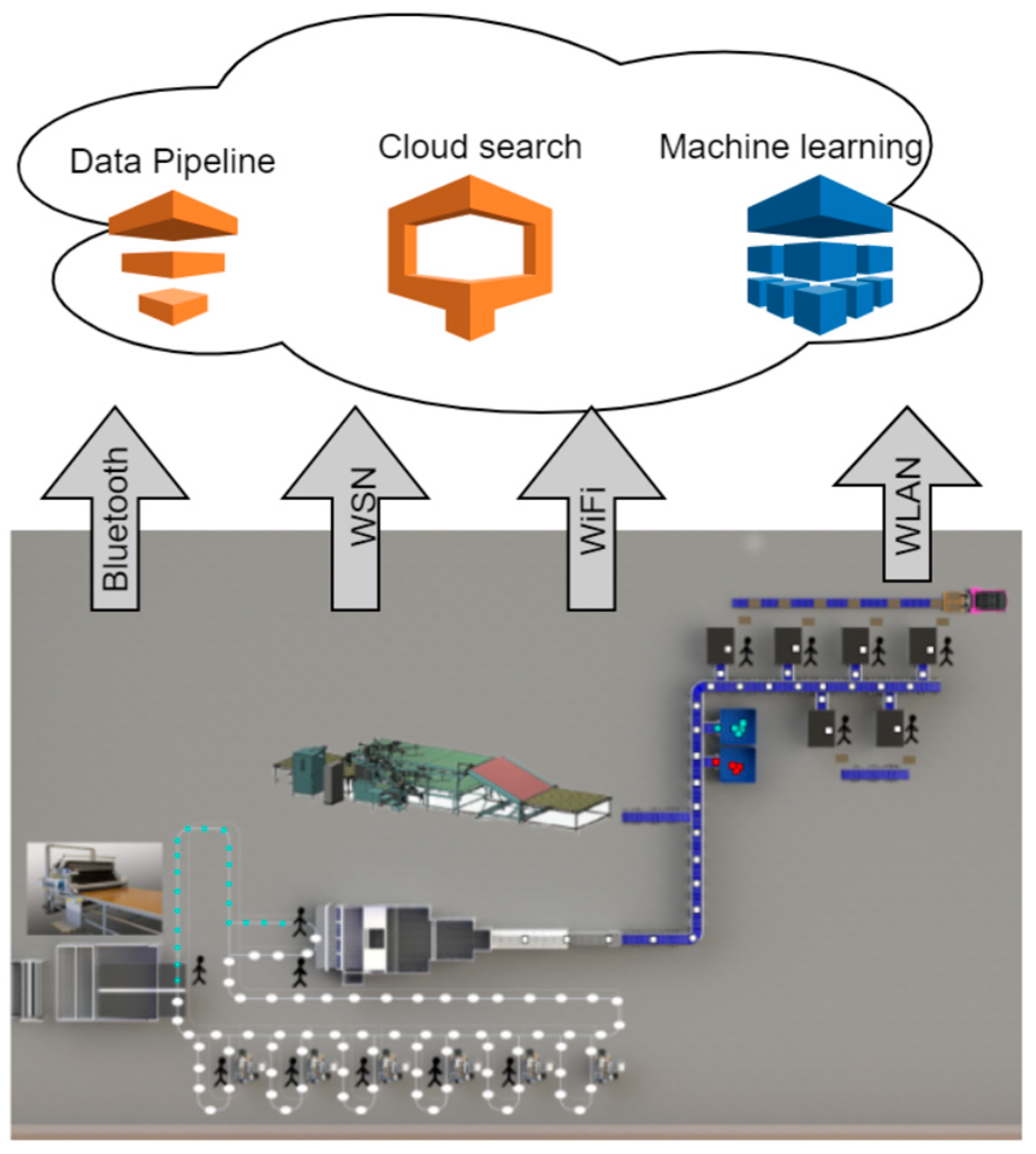
NSM data loading process. The process for determining what information... | Download Scientific Diagram